Phishing is a cybercrime in which targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing:
-
- sensitive data such as personally identifiable information,
- banking and credit card details
- and passwords.
Objective
History of Phishing
-
- Phishing techniques were described as far back in 1987, but the term was first used in 1995/1996
- Some other early phishing scams were in 2003 when emails that looked to be official correspondence from eBay stated that the user needed to make updates to their accounts
Why Is Phishing a Problem?
-
- Cybercriminals use phishing because it’s easy, cheap, and effective.
- Email addresses are easy to obtain, and emails are virtually free to send. With little effort and little cost, attackers can quickly gain access to valuable data.
- Those who fall for phishing scams may end up with malware infections (including ransomware), identity theft, and data loss.
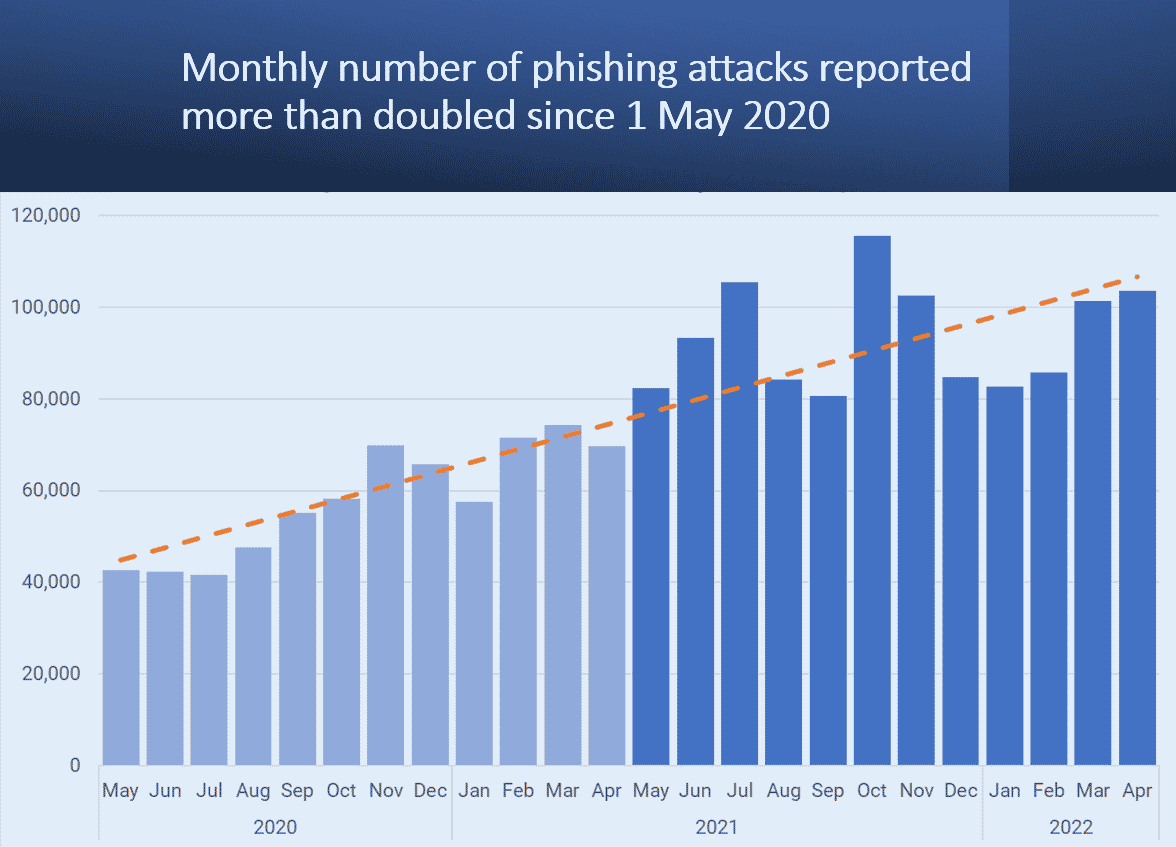
Report trends of Phishing
According to www.apwg.org we get :
INTERISLE STUDY SHOWS 61% INCREASE IN PHISHING ATTACKS, MORE BRANDS TARGETED, AND 257% INCREASE IN CRYPTOCURRENCY PHISHING
Type of Phishing Attacks
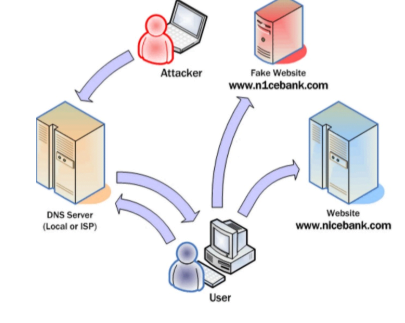
- Pharming Attack
In recent years, both pharming and phishing have been used to gain information for online identity theft.
Pharming don’t require attacker to send mail, Instead attack server.
Pharming has become of major concern to businesses hosting ecommerce and online banking websites.
How does it work?
- Phone Attack

- Deceptive Phishing
How does it work?

- Spear Phishing
How does it work?

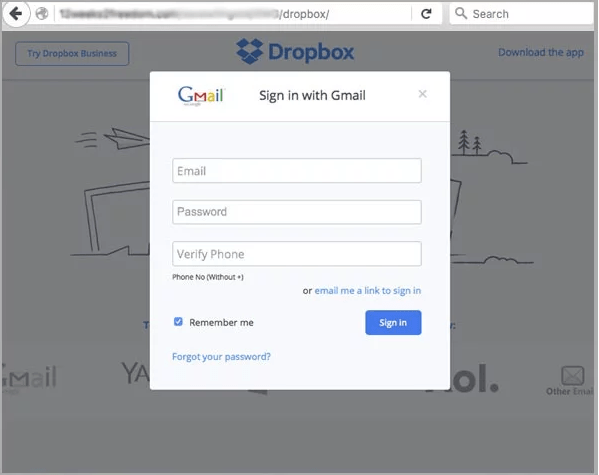
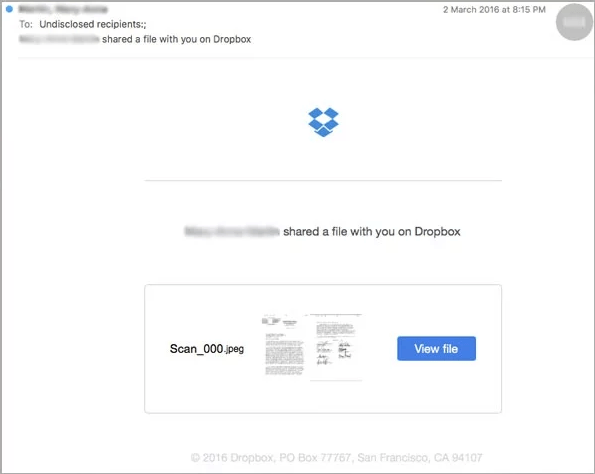
- Dropbox Phishing
- Dropbox, the handy Cloud based storage for files
-
- Dropbox had over 500 million registered users
- around 1.2 billion files uploaded to Dropbox every day and 3.3 billion shared connections
- Phishing Attack
-
- Phisher create form that similar to dropbox
- they noted target who they want to attack and what they want about victim’s
- Then they send email asked the user to click on a link to open file or download file
- If victim click on link to download or open (the file mostly have ransomware if downloaded, it can install on victim’s computer)
- and some another ask user about information like account detail or bank account if you completed what they ask you will loss your information.
- Example
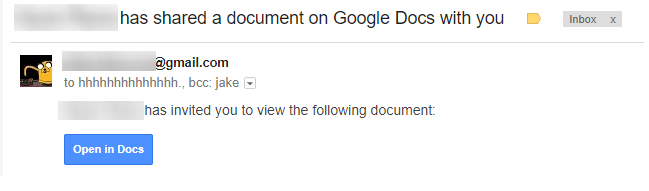
- Google Docs Phishing
Example
Solution and Defending
To prevent the phishing :
- Keep Informed About Phishing Techniques
- Think Before You Click!
- Install an Anti-Phishing Toolbar
- Check Your Online Accounts Regularly
- Keep Your Browser Up to Date
- Never Give Out Personal Information
- Use Antivirus Software
- Be Wary of Pop-Ups
Conclusion
Phishing is a form of social engineering used to collect personal information from the intended victim. Phishing campaigns have existed for quite a while and continue to increase in attempts and sophistication. It is important to stay aware of the phishing trends and to keep your computer and internet browsers up to date with current antivirus and security patches. These methods may not keep you 100 percent safe, but are the best way to try.
Reference
- http://www.phishing.org
- https://searchsecurity.techtarget.com
- https://www.tripwire.com
- https://securingtomorrow.mcafee.com/business/data-security/past-present-and-future-of-phishing/ By David Bull, Jun 09, 2015
- https://inboxpros.com/top-phishing-trends-2017/
Category :